Risk Resources For Insurance Companies
Everything You Needed To Know For Risk Consulting In One Place!
Incident Response Planning Services
Do you know what your business would do if it were hit with a data security breach? Studies show businesses with an incident response plan in place when a breach occurs suffer less economic and reputational harm while also returning to business more quickly than those that have not prepared...
Applying the Resources of a Cyber Policy to a Cyber Incident
Ransomware attacks have increased and monetary demands have tripled over last year. This program will begin with an overview of claims trends in the cyber arena. An interactive case study of a ransomware attack has been prepared. A group of experts consisting of: Insurance Claims Counsel, Cyber Breach Coach, Forensics...
Insurance Industry Buzzes Over Data Breach Ruling
If the rash of data breaches in recent months has done anything for businesses, it's raised their awareness of cyber liability insurance. The market for cyber liability insurance is expected to increase dramatically as businesses become more aware that their current policies don't adequately cover cyber-risks, according to the National...
Early Data Breach Insurance Case Discusses Cyber Policy Coverage for Traditional Risks
Last May, we told you that the “waiting has ended“ for courts to start weighing in on cyber insurance policies, as the District of Utah issued one of the first federal court decisions construing such a policy in Travelers Property Casualty, et al. v. Federal Recovery Services, Inc., et al.,...
Cyber Insurance: Preparation for a Breach
Managing risk in a digital infrastructure is an increasingly complex and challenging problem, one that can’t be completely mitigated through technology, and the cost of data breaches are increasing. The average organizational cost of a data breach in the U.S. is $5.85 million. The average cost of data breach notification...
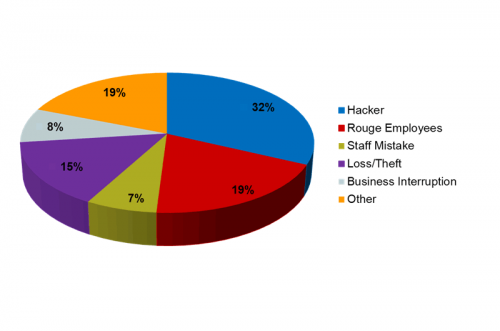
Data Breach Causes
Where are the threats? Inside threats –Employee negligence Security failures Lost mobile devices –Employee ignorance Improper disposal of personal information (dumpsters) Lack of education and awareness –Malicious employees Outside threats –Hackers Malware Phishing and Spear Phishing –Thieves (including Social Engineering Tools) –Vendors
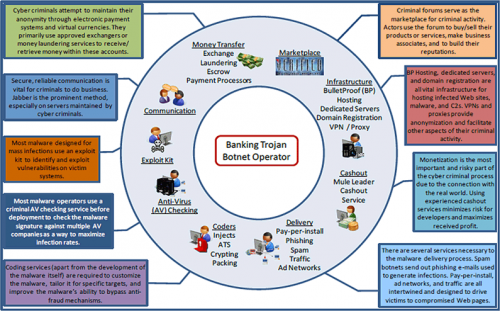
The Cyber Underground
Money Transfer - Exchange Laundering Escrow Payment Processors Cyber criminals attempt to maintain their anonymity through electronic payment systems and virtual currencies. They primarily use approved exchangers or money laundering services to receive/retrieve money within these accounts. Communication Secure, reliable communication is vital for criminals to do business. Jabber is...
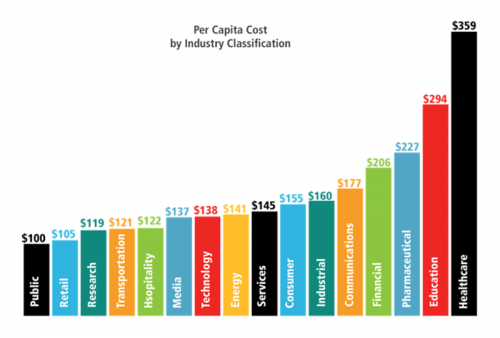
Is Your Company Ready For A Data Breach?
Data Breach Costs per Sector The cost of a data breach can vary significantly by industry, due to differences in the types of data collected and various regulatory and compliance obligations. A recent study showed that healthcare currently expects the largest cost, at an average of $359 per record. Note...
Risk Consulting Resources
- Articles Worth Reading (1)
- Crime (1)
- Cyber Liability (5)
- Financial Institutions (3)

Leverage the breadth and depth of our education, experience and vision to deliver solutions to you.




 All Risk Consulting Resources
All Risk Consulting Resources